AM NOT A EXPERT AND THIS IS NOT A HOW TO DO IT
This is a project that been built over time and when I have a moment. It been a learning experience as I been going through this. A lot of code is provided from ChatGPT but a lot of the logic and thinking has come myself.
The Overview and madness
I started one day with looking how much rubbish traffic is coming in to my routers. PFsense does a pretty tidy job at dropping this but then i wondered is there a way I can tell it to drop before snort kicks in. The moment of Lionel Hutz with a voice of why you looking in my window. I decided to explore where traffic comes from on a server that does “Nothing”. With a free Sunday I decided to see if we could get a script together that does the following:
- Capture the IP address of who is trying to access the server
- Get what port they are trying on and what service they trying it with
- Make sure I got the ASN number to help tie up the attack with a provider
- Report back to a dashboard
- Produce a block list of who is sending me it’s traffic
With this in hand I did need to look at a few points of what do I do with this information. Also how to go about setting this goal to work with out comprising my network. A few factors to consider with this when I created the project:
- How do I keep my network safe
- I am working with a MYSQL database how to I make sure the access for it is protected.
- Is this really the rabbit hole I want to go down
In a nutshell what is the over all set up
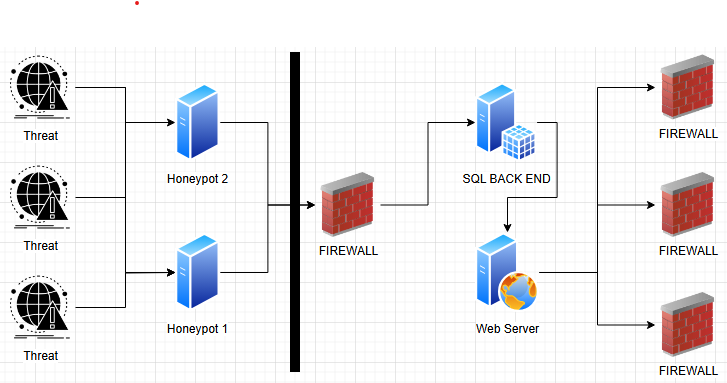
The process for this starts when a IP address connects on one of my “honey pots”. These are hosted on 3rd party provides. The Joys of £1 / 1$ (70p on last rebuild) VPS. All they have is the basic spec of Debian, no more than 1gb ram and 10gb disk. No frills needed as with the goal I just need it to accept connections.
What I want to happen is Rouge IP to connect to the honeypot on any port. To be clear this server does nothing. It runs a Python script and that is everything. Nothing a normal person would connect to or have a need to. No domain name pointed at it, no real traffic there.
When a IP address connects to it what happens is the server accepts the connection and returns a valid response code. At the same time this happens the python script collects the IP address, port number, username and password of what they trying to use to connect. Once we have this information it also looks up to see the ASN, Provider, Country and location of the ip address.
On this duly note, I did also change the SSH port to the remote servers. Nothing like getting myself banned in all this.
We also have some extra spice to this Honeypot, I run fail2ban to block a IP address after a 2nd attempt. No point letting it have free rain to keep trying.
Let’s cross that black line on the chart
Next we then pass this back to a MYSQL database where it stores in the main table for 30 days before sending it off for deep storage aka I export it once a month and use it for other purposes. To secure the MYSQL a strong password is in use and also on the firewall that handles the SQL location I operate a allowed traffic policy. Also the ports are changed.
With this a Cron job is run to handle the tidying up of data. The first time I ran this it took 30 minutes to move over 3,000,000 rows of data. this is now a more manageable level as some of the data may change or become useless.
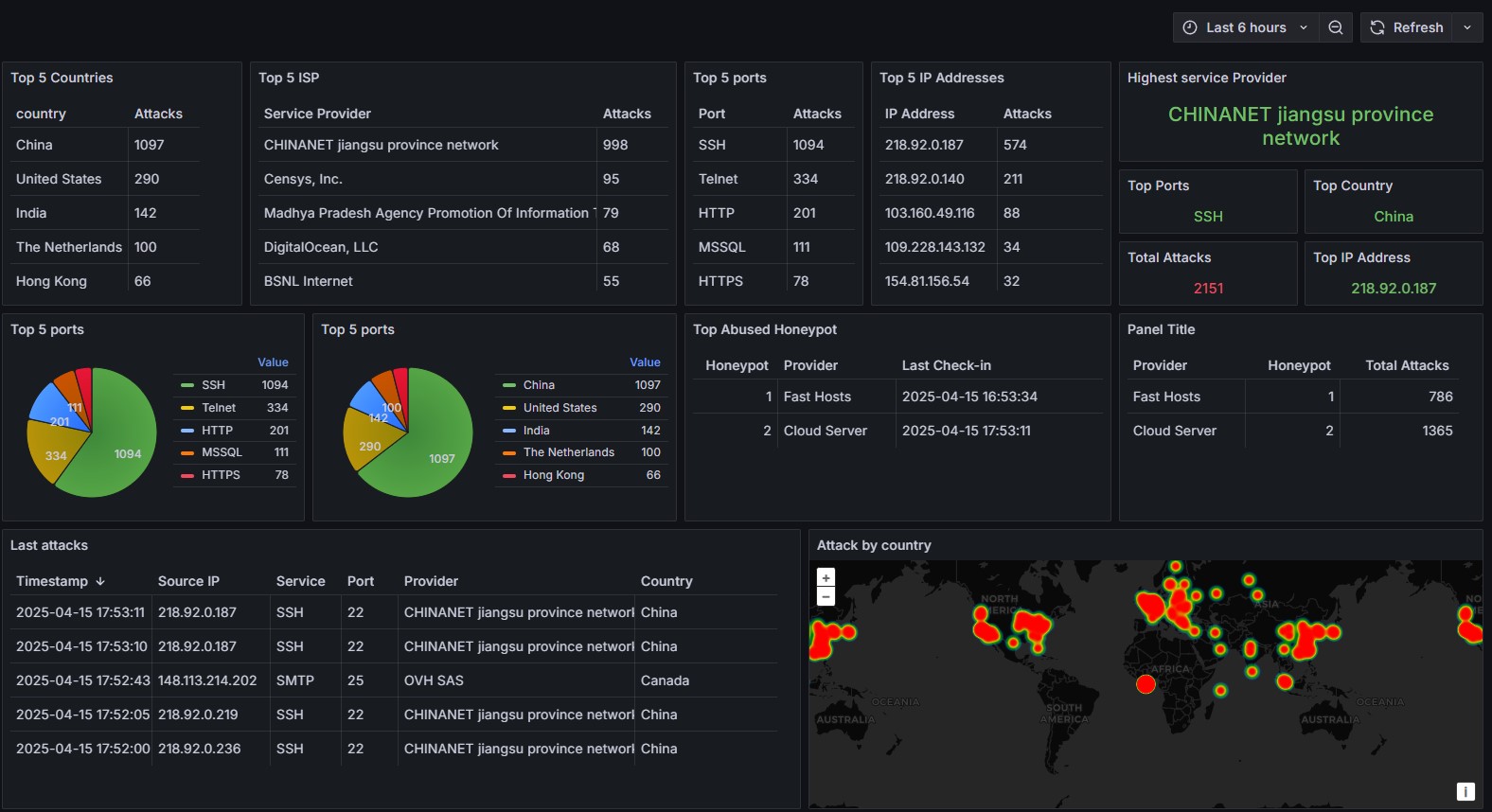
With handling the data next up is to get it in to something graphical that looks appeasing on a wallboard in our office. Clients visit our office and as they come in they see our network war board or as the office manager describes it “I am seeing a lot of red that is not the normal suspects”. One of the big things here is it becomes a talking point. I pick the data up from Mysql and then fire it to Grafana to handle the visuals. This gives us a very pleasing dashboard which people can see.
The Python script also get the details from IPinfo to help show the ASN + country + provider.
We have data, I have a pleasing on the eye graph but what else?
Now this data has some other use than being a talking point. I look after 10 firewalls which all rely on snort to do detection. It doe’s a nice job but in some sense do I want to wait for it to attempt a few times before snort kills it. What I can do is now get a management interface in PHP to communicate with the SQL. This now allows me to create a filter and lists of ASN + IP addresses + countries I want to give the block to. Each one it’s own text file which is generated every 4 hours. This means it will take off old ip addresses that no longer a threat. With this the lists are produced 4 hours, 24 hours, 7 days and 30 days.
With using filters we can then set it to what I want the firewalls to actually drop. I can use the edge firewalls to drop more traffic at a core level before it hits down to a firewall further down the line. This means high risk traffic could be stopped before the firewalls with slower connections are impacted. When I use the lists I also have a allow list that fail safes a few ASN numbers and IP addresses from being included in a block list. Further planning says if they appear in the list I want to get a alert so a member of my team can go and hunt down the issue.
Further considerations
I would like to pass this over a API but found it became frustrating to get the data to pass nicely. It would create a safer layer around the data insert but at the same time I just need a another rainy day in Essex on a Sunday.
Also I do hope to make this project a bit more sharable for people to run. It not aimed at massive companies but us nerds. I got a few people in work who are data driven and like a good bit of data splatter.
Same time I want to also make it so the data is opensource on to Github so people can download the lists if they wish to. At the moment the feeding out to the firewalls is a mixture of Edgerotuers, PFsense and Mikrotiks.
Closing words
I do have to end this with a final few words, This is not my full time job. Am not a expert but this is just been a little project when I been bored. A lot of this been built with AI but a lot of the logic and workflow is something I need to work with. AI has provided some code but I still had to sanity check it. This project could be recreated.
Plus the thought of this might need a name for this project. “Honeypots” Is more a working name.
Further reading I would recommend checking out this article from Mythical Beasts. They are not one of the provides my VPS’s sit on.